A week after Adobe, Microsoft, and Mozilla announced several patches to address multiple vulnerabilities, Google’s Chrome announced it’s own update to patch 62 security issues. Coincidentally, Adobe released an additional “out of band” update for it’s Flash Player with another patch to be released the next week to address a secondary issue.
By now, you may have heard about one of the latest instances of malware to effect Apple’s operating systems. This malware dubbed WireLurker has shown that there is an increased movement in targeting Apple users who for years have indicated that Macs just don’t get viruses. The articles below also point out the dangers of jailbreaking a phone and installing third-party apps and run an up-to-date antivirus on Mac operating systems.
http://www.scmagazine.com/the-command-and-control-server-for-wirelurker-has-been-taken-offline/
Below are recommendations provided by Palo Alto Networks to help prevent WireLurker and similar threats:
- Employ an antivirus or security protection product for the Mac OS X system and keep its signatures up-to-date
- In the OS X System Preferences panel under “Security & Privacy,” ensure “Allow apps downloaded from Mac App Store (or Mac App Store and identified developers)” is set
- Do not download and run Mac applications or games from any third-party app store, download site or other untrusted source
- Keep the iOS version on your device up-to-date
- Do not accept any unknown enterprise provisioning profile unless an authorized, trusted party (e.g. your IT corporate help desk) explicitly instructs you to do so
- Do not pair your iOS device with untrusted or unknown computers or devices
- Avoid powering your iOS device through chargers from untrusted or unknown sources
- Similarly, avoid connecting iOS devices with untrusted or unknown accessories or computers (Mac or PC)
- Do not jailbreak your iOS device; If you do jailbreak it, only use credible Cydia community sources and avoid the use or storage of sensitive personal information on that device
Additionally, it should be noted that there is a variant of this malware available for Windows and that Palo Alto Networks has provided a tools on their GitHub site to detect WireLurker for both Mac OS X and Windows operating systems.
On October 14th, Adobe released security fixes for an issue in Adobe Flash Player version 15.0.0.167 and earlier (the current Mac and Windows version as of this posting is 15.0.0.189 and version 11.2.202.411 for Linux users). The impact of this vulnerability could allow an attacker to take control of an affected system and be exploited during a drive-by download attack. This type of attack can happen by visiting a malicious website viewing an email message with embedded multimedia or clicking on a deceptive pop-up window.
Please visit http://helpx.adobe.com/flash-player.html to check to see if your computer is impacted. If you need to take action, you will be prompted to update your version of Flash.
For Google Chrome users, patches for Adobe Flash have been incorporated into the latest release of the browser and will be updated automatically.
As for Adobe Air, users are able to check their version by following the instructions provided on Adobe’s website at http://helpx.adobe.com/air/kb/determine-version-air-runtime.html. If you are unable to verify the version trough this method, double-check to see if to see if the software is even installed via the Control Panel in Windows or in the Application/Utilities folder on a Mac. If Adobe Air isn’t present in either of these instances, you will still need to verify your version of Adobe Flash.
Microsoft released patch KB300869 to address CVE-2014-4114 which allows an attacker who successfully exploits this vulnerability could run arbitrary code in the context of the current user. If the current user is logged on with administrative user rights, an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
Windows users are asked to update their there systems immediately:
Windows 7
http://windows.microsoft.com/en-us/windows7/install-windows-updates
Windows8 and 8.1
http://windows.microsoft.com/en-us/windows-8/windows-update-faq
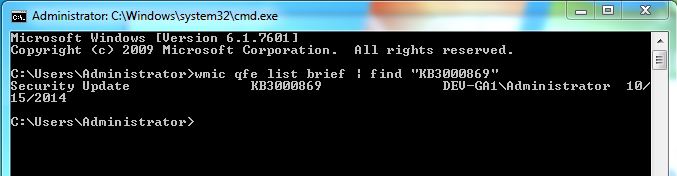
Once the latest patches have been installed, system owners can verify that the patch has been applied by pasting the following line into a command line window (Start; goto Run; and type: cmd.exe; hit Enter)
wmic qfe list brief | find “KB3000689”
The expected output should look like:
For more information about this vulnerability:
http://www.isightpartners.com/2014/10/cve-2014-4114/
Yahoo CISO Alex Stamos refuted claims made by a Louisiana security company that a number of Yahoo servers had been compromised by Romanian hackers using Shellshock exploits against the vulnerability in Bash.
Stamos said three Yahoo Sports API servers were infected with malware by hackers looking for webservers vulnerable to the Shellshock vulnerability, but the exploits were not related to Shellshock. Those servers, which provide live game streaming, do not store user data and were isolated upon discovery of malware, Stamos said.
http://threatpost.com/yahoo-confirms-infected-servers-unrelated-to-shellshock/108726
Internet2 is actively monitoring and assessing shellshock’s impact on the Internet2 community and working with its partners to rapidly update open source development packages it supports.
https://www.internet2.edu/products-services/support/internet2-shellshock-update/
Computerworld magazine posted in an article on September 26, that the number of stores effected by this breach had increased from 108 to 216 (http://www.computerworld.com/article/2687802/data-breach-that-hit-jimmy-johns-is-larger-than-first-thought.html?source=CTWNLE_nlt_security_2014-09-29#tk.rss_security0).
Jimmy John’s as released a statement addressing this issue and provided a utility to search store location effected by this incident of which two location are in Springfield:
https://www.jimmyjohns.com/datasecurityincident/storedates.html
US-CERT is aware of a Bash vulnerability affecting Unix-based operating systems such as Linux and Mac OS X. Exploitation of this vulnerability may allow a remote attacker to execute arbitrary code on an affected system.
Apple’s iOS 8 addresses a serious weakness that could allow attackers to hijack the wireless network authentication of Apple devices and gain access to enterprise networks.